Application Security Risk Assessment
Our team of AppSec experts have experience across a wide range of programming languages and technologies to help you confidently secure any type of application.
Go Beyond Pentesting
Pentesting is a commonly used approach to test the security vulnerability of software applications, but it doesn’t give you the full picture.
Using OWASP’s Application Security Verification Standard (ASVS), and MASVS for mobile apps, our end-to-end Application Security Risk Assessment goes beyond pentesting. We have expertise with mobile (iOS and Android), Web (SPA, traditional, and PWA), API (REST, GraphQL), and IoT.
We follow a four-stage process including a discovery and design review, threat modelling, pentesting including code and vulnerability analysis, and risk assessment to deliver a comprehensive report of your application’s security posture.
This is a more complete analysis than pentesting alone and provides your team with a clearer path forward to securing your organization’s most valuable assets.
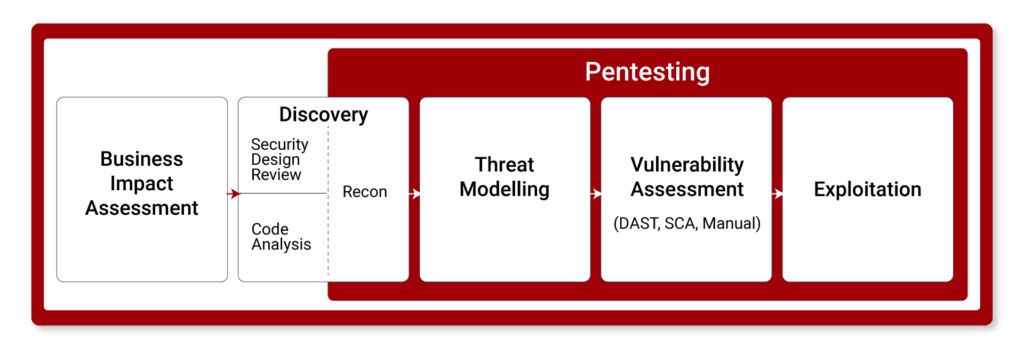

Our Four-Stage Process
1. Discovery
Understanding the architecture of an application is essential to ensuring no potential threats go unnoticed during the assessment process.
Our security consultants will work closely with your team to get an understanding of your application to inform our approach. This can include hands-on design workshopping and full documentation for your organization.


2. Threat Modeling
Based on the security design output, threat modelling will be conducted to identify key threat scenarios specific to your application.
We use the STRIDE scheme to classify threat scenarios and an enhanced DREAD model to assign the specific impact and likelihood levels to determine the risk for each identified issue, which will be reviewed with your team.
3. Pentesting
Using OWASP’s detailed ASVS assurance criteria, our security team will build and execute test cases using manual and automated methods, including source code analysis, where applicable.
This will enable us to verify each threat scenario and identify the actual risks to your business.
4. Finalization
Once our Application Security Risk Assessment (ASRA) is complete, your team will receive a detailed report that clearly outlines all security risks based on impact and likelihood. This makes it easy for your team to prioritize what’s most important to your organization.
This report also comes equipped with recommended controls to support business risk management decisions.
Our Packages:
| Level 1 | Level 2 | Level 3 |
|
|---|---|---|---|
| » Application Security Verification Standard (ASVS): | Level 1 (Apps with low assurance needs) | Level 2 (Recommended for most apps) | Level 3 (Critical apps needing high trust) |
| » Manual and Automated Testing | Included | Included | Included |
| » Security Design Review | None | Standard | Detailed |
| » Threat Modeling | Basic | Standard | Detailed |
| » Automate Code Analysis | None | Optional | Included |
| » Manual Code Analysis | None | Optional | Optional |
| » Duration | 2 – 4 Weeks | 3 – 6 Weeks | 4 – 8 Weeks |