With attacks on the rise and attackers continously evolving, so too should your testing approach. Our team of experts replicate real-world threats to find weaknesses in your security.
Penetration Testing for Application and Cloud
Enhance your security posture
The 3 Types of Pentesting
Black box is when the pentester has no knowledge of the information, essentially they are presented with a black box, and they are asked to identify the security problems, and to try to exploit it.
White box is where the pentester is given all the knowledge about the system, including internal design and access so that they can fully understand the blueprint and really dig deep and identify all the security issues.
Gray box is somewhere in between. This is where the pentester is provided with some level of information and is expected to perform their pentesting activities.
Penetration Testing
vs Vulnerability Assessment
Pentesting is not the same as a vulnerability assessment and, unfortunately, oftentimes the two are confused.
Pentesting is known as ethical hacking, and is a process by which you try to penetrate a given system.
Vulnerability assessment is a process by which you try to determine the weaknesses of a given system. This can be done manually or using automated tools.

The tools can often provide a false sense of security because they have a lot of false positives and don’t take into consideration the risk – which is a combination of the likelihood and impact to the business.
This requires a person with knowledge of the business and security architecture to manually triage and remediate the issues. Whereas tools only know as much as the rules they have been provided.
Vulnerability assessment tools produce severity ratings that are generic and baseline industry information without taking into a context your assets and the business impact that could happen if those assets were on under attack.
Pentesting takes the result of that and tries to combine those vulnerabilities to see if there are opportunities to actually exploit the system.
Book your Annual Pentest
Attackers are shifting their focus to software applications, which means it’s never been more critical to ensure a strong application security program for your organization. All of our assessments are performed in-house by a team of software experts.
How Often Should You Do Pentesting? Read the Blog.
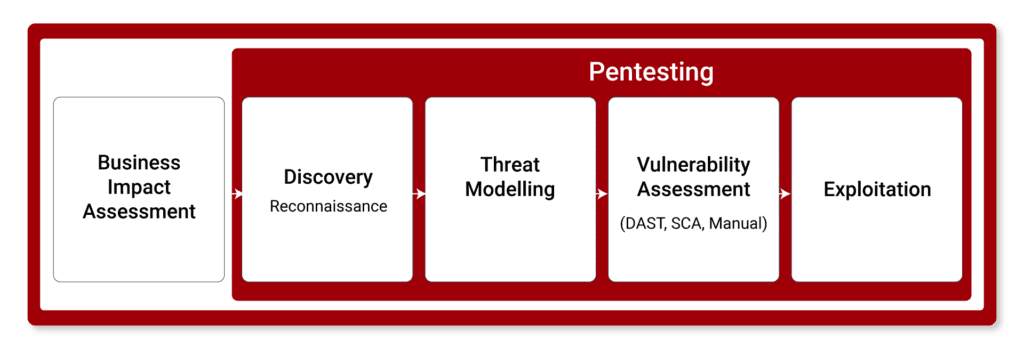
Go Beyond Pentesting 4-Stage Application Security Risk Assessment
Pentesting is a commonly used approach to test the security vulnerability of software applications, but it doesn’t give you the full picture.
Using OWASP’s Application Security Verification Standard (ASVS), and MASVS for mobile apps, our end-to-end Application Security Risk Assessment goes beyond pentesting. We have expertise with mobile (iOS and Android), Web (SPA, traditional, and PWA), API (REST, GraphQL), and IoT.
We follow a four-stage process including a discovery and design review, threat modelling, pentesting including code and vulnerability analysis, and risk assessment to deliver a comprehensive report of your application’s security posture.
This is a more complete analysis than pentesting alone and provides your team with a clearer path forward to securing your organization’s most valuable assets.
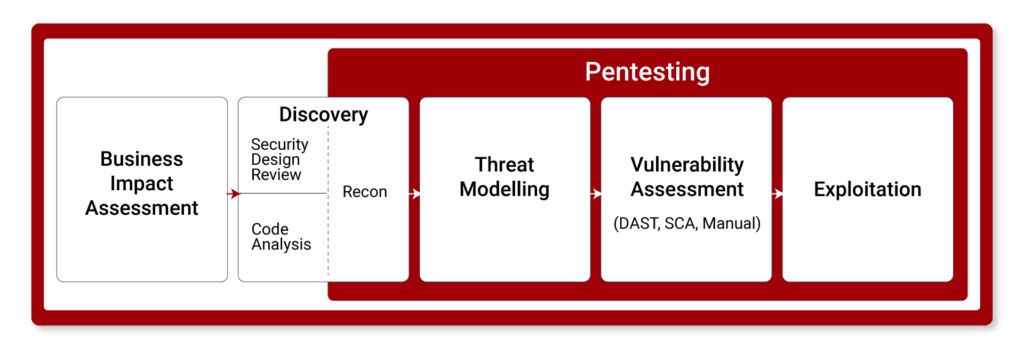
How to Choose a Pentest Provider?
When choosing a pentesting provider, there are the two major considerations:
- Does the provider follow standard practices such Open Web Application Security Project (OWASP) and Security Verification Standard (ASVS)?
- Are the pentesters familiar with applications and software development? Often the pentesters might have a network background but does not understand anything about software, and you won’t get the best results from the pentest.

Why Choose Forward Security?
At Forward, we’re proud to offer an application security team made up of ex-software developers who have the specialized knowledge and experience in fintech and finserv, health-tech, eCommerce, and technology providers. Partnering with global organizations, we are familiar with the many standards, regulations, and systems of each of these domains.
Where we focus
We Standardize with OWASP ASVS & CIS Benchmarks
The OWASP Application Security Verification Standard (ASVS) & CIS Benchmarks provide a basis for testing application technical security controls. We follow ASVS, CIS, Cloud Security Alliance (CSA) and other industry best practices. This enables us to break down access control into granual steps to look for specific issues and test cases. In addition, it provides a repeatable and standardized process so that nothing gets missed and we deliver consistent results, every time.
Have You Booked Your Annual Penetration Test Yet?
Strengthen your security posture while proving compliance. Our annual penetration tests help you identify and remediate critical vulnerabilities in your cloud or application. For a deeper level of investigation and protection, we recommend performing at least one comprehensive application security risk assessment, which includes: Discovery, Threat Modeling, Penetration Testing, and Finalization.
How Often Should You Do Pentesting? Read the Blog.