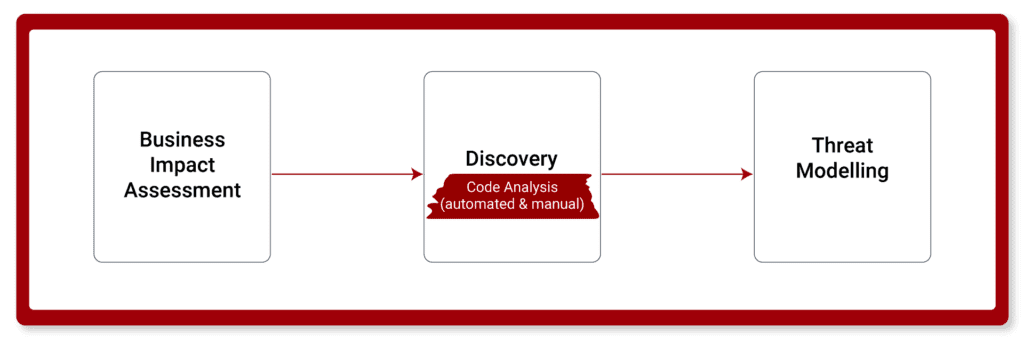
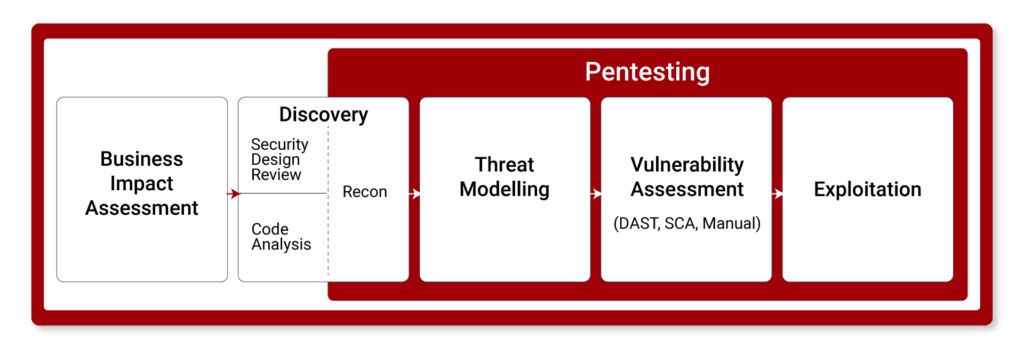
Code security and vulnerable dependency analysis is the process of manually checking the source code of an application for security issues.
Since many significant application security issues are extremely difficult to discover with other forms of analysis, such as penetration testing, this makes code security analysis the ideal method for technical testing