The Background
Our client in the data analytics sector had implemented DevOps automation and CI/CD pipelines but without any security in the mix. This is quite common as some organizations often focus their resources heavily on product development, especially in early stages of growth with security being an afterthought.
Normally, organizations should have SAST and SCA executed in the CI part of the pipeline, which involves checking and building the code. DAST is usually integrated in the CD part of the pipeline that deploys and runs the application. However, our client did not have security automation tools incorporated in any stages of their pipeline.
Without these scans, it takes a reviewer a lot of time (and money) to do manual assessments, which are also prone to mistakes (either missing something due to not knowing what to look for, or overlooking something due to human error). As a result, there is a higher likelihood of security (and other) issues being missed if only manual testing is conducted.
Most organizations engage pentesting providers once per year. However, in between each of these annual assessments is a gap where new code is written, and vulnerabilities arise in new and existing packages that are not scanned. Due to the time, cost, and complexity required make it prohibitive every time there is a change to the application.
An optimal solution is to use automated security scanners in the CI/CD pipelines to catch the low-hanging fruit along the way leading up to the pentest, but herein lies the first set of challenges.
The Problem
Installation and orchestration: Each new scanner that gets added to the pipeline needs to be installed into the CI/CD build agent. If you have multiple build agents, you may end up installing them on different machines, manually configuring each of them, maintaining them, and ensuring they are always up to date. There is no consistent and unified way to manage and configure multiple scanners. While some of this process can be automated, there’s still a bit of work involved, and it can be complicated. Today’s applications make this more challenging due to the varied technologies used to build applications, each requiring a different type of scanner.
Aggregation and correlation: When you run multiple scanners, what you end up with are data in different formats and in different places. Trying to manually aggregate, normalize, and correlate the issues is mundane, time-consuming, and prone to error. Furthermore, as testing frequency increases in modern architectures and methodologies, more data is produced that needs to be processed.
Without correlating similar findings, it’s more difficult to triage issues and identify actual problems. The overwhelming volume of issues reported requires a great deal of effort to review and evaluate, often resulting in false-positive fatigue.
The Solution
To address these challenges, we deployed the Eureka DevSecOps Platform. Eureka enables you to centrally install and orchestrate your application security scanners (such as SAST, SCA, DAST, and others), aggregate and correlate the results, and manage the threats and risks.
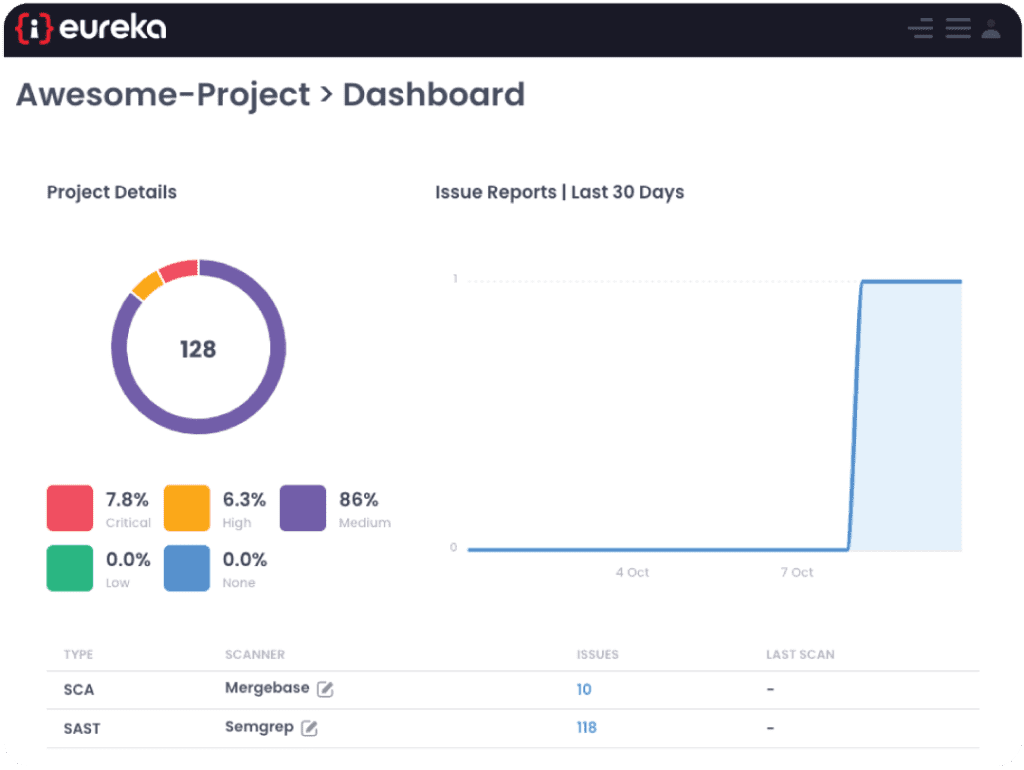
This enabled our client’s development team to get the most value from the security automation tools selected, and better identify actual security issues.
How the Eureka DevSecOps Platform helps with installation and orchestration: Eureka makes it easy to integrate and centrally configure multiple scanners. All scanners will automatically run inside of the Eureka Agent so our client doesn’t need to deal with individual installation, configuration, and maintenance.
How Eureka helps with aggregation and correlation: Eureka uses proprietary technology to identify similarities between issues found by different scanners and groups them together. This reduces the number of vulnerabilities that developers need to review, eliminates false-positive fatigue, and allows real issues to be discovered.
Adding security into our client’s pipeline without any additional complexity and scanners to manage has saved them a lot of time, money, and stress. They are now able to get more value from their security investment while reducing their business risk.
With Eureka, you can:
-
- Bring Your Own Scanner (BYOS) (commercial or open source)*
-
- Centrally configure and orchestrate your scanners
-
- Easily integrate your scanners with CI/CD pipelines*
-
- Run the scanning agents inside your own environment
-
- Keep the scan data in your own environment for maximum privacy
-
- Correlate security issues to reduce false positives
-
- Filter and push issues to your issue tracking system*
-
- Join security issues to create threat scenarios and assign risk
-
- Get better view of risks based on data from manual and automated processes
* Currently supporting Jenkins, GitHub Actions, and Azure DevOps Pipelines, and Jira
How Mature is Your DevSecOps?
Our comprehensive DevSecOps Maturity Assessment covers 8 key phases of DevSecOps practices, 29 questions in total.
By evaluating your team on each capability, you can determine if your DevSecOps maturity level is early, intermediate, or advanced. Your assessment includes a custom report that provides your overall maturity as well as detailed recommendations you can take to enhance your security posture.


