As the rate of application adoption accelerates globally, teams are expected to produce software faster, and often under tight budget and timelines. This provides an increased level of opportunity for attackers to use application as an attack vector. According to the 2023 Verizon Data Breach Investigation Report, attackers leveraged applications in 80% of incidents and 60% of breaches, and these numbers continue to rise.
SAST, SCA, DAST, ASOC, ASPM, Threat Modelling, the alphabet soup of Application Security acronyms goes on… But what does it all really mean, and how can you make application security simple and effective? That’s a question that we grappled with as developers, as do many others out there! The current landscape of tools and processes can be daunting and complicated, and we are here to help make sense of it all.
Challenges Development Teams Face
Development teams face a myriad of obstacles when it comes to securing their software. Application security can be complex and time consuming, requiring multiple tools and subject matter expertise. Since modern software is composed of custom code combined with many 3rd party packages, Static Application Security Testing (SAST) and Software Composition Analysis (SCA) tools are required at a minimum. In addition, Dynamic Application Security Testing (DAST) is required to interact with the running application and identify issues at run-time.
While there are many tools that cover these types of scans, they need to be individually managed and the results are often spread across different reports or portals. Management and integration of each tool in CI/CD individually, and trying to find real vulnerabilities among those reported require additional effort. On top of that, aggregating and correlating the results from different tools to find relationship between the vulnerabilities reported can be time consuming and erroneous. Threat modelling is also required to identify which combination of vulnerabilities pose the highest risk. As a result, development teams end-up needing assistance from Application Security subject matter experts who are in short supply.
Furthermore, each type of scanner is looking at the application from a different lens, and expertise is required to identify similarities or relationships between the vulnerabilities to determine which ones to prioritize. To add to all this, most tools do not map the vulnerabilities to application security requirements resulting in no traceability from development to testing.
There is a missed opportunity to better what to fix with limited resource, get more value from the investment in security, and reduce business risk.
The Solution: Orchestration, Aggregation, Correlation, Threat Modeling
Given the multitude of tools and sources of vulnerabilities developers are faced with and the resource constrains, a platform is needed that centralizes management and orchestration of tools, aggregation and correlation of results, and provides the ability for developers to trace vulnerabilities back to security requirements.
In addition, developers should be enabled to perform threat modeling with relative ease and assess the risk of each threat scenario to be able to prioritize based on business context. These capabilities allow the developer to address the low hanging fruit with less reliance on subject matter experts and deliver secure applications to market quicker.
Meet Eureka, the DevSecOps Platform
The Eureka DevSecOps Platform brings these features under one roof and makes it easy to centrally manage and orchestrate multiple scanners (SAST, DAST, SCA) within CI/CD pipelines. The selected scanners (with Semgrep as the default SAST tool) are automatically orchestrated by the Eureka Agent that runs inside the client’s environment, alleviating the need to deal with individual installation, configuration, and maintenance.
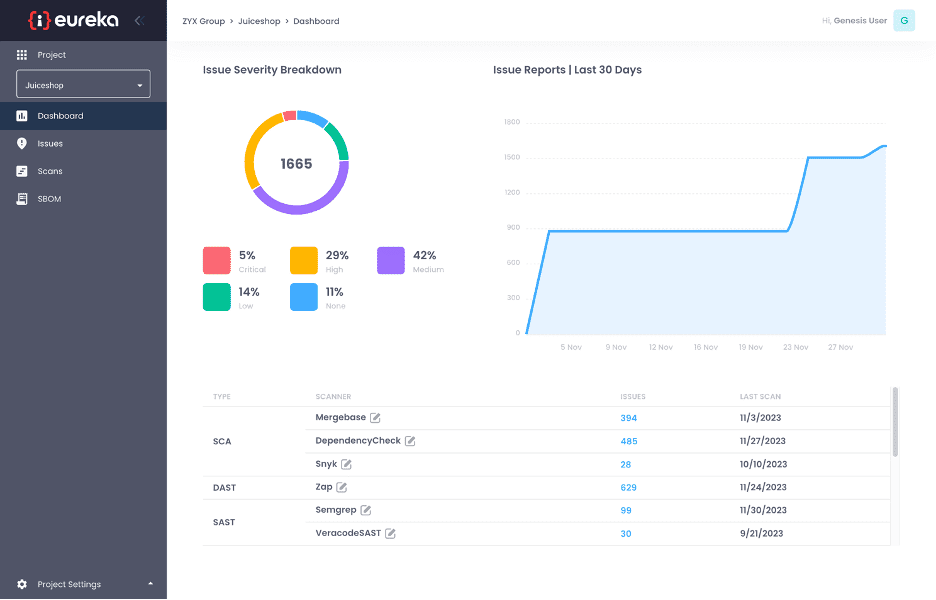
Eureka uses proprietary technology to identify similarities between issues found by different scanners and groups them together based on OWASP’s Application Security Verification Standard (ASVS) requirements. This provides the opportunity for developers to focus on requirements such as those related to authentication and session management that must be addressed first, before focusing on fixing those from other categories. Aggregation and correlation across results from different scanners, with the ability to perform threat modelling and risk assessment on the remaining vulnerabilities allows developers to focus on the vulnerabilities that pose the highest risk, while reducing false-positive fatigue.
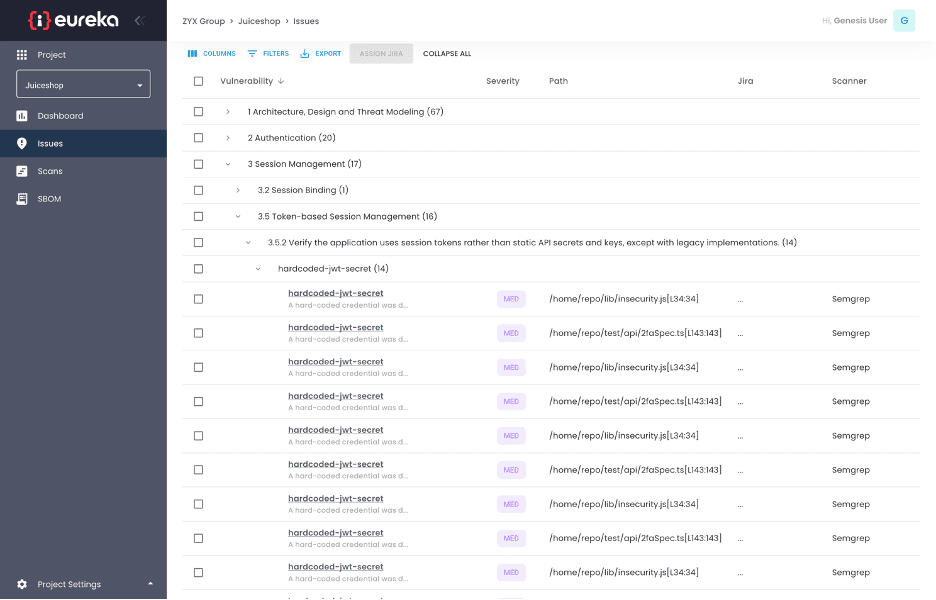
Once the developer has determined which vulnerabilities needs to be addressed, they can be added to the existing issue tracking system to avoid having yet another place to check for what to fix.
In addition, the hybrid installation option allows storage of all vulnerability and threat related date to be stored within the client’s own cloud environment, providing maximum privacy and the same benefits as an on-prem solution, without all the installation and maintenance headaches.
Meet Semgrep, Application Security Platform
Semgrep’s application security platform is built for engineers so they can fix the issues that matter before production. Semgrep scans for vulnerabilities in code with its SAST capability (Semgrep Code), known supply chain risks using its SCA engine (Semgrep Supply Chain), and accidentally committed secrets using the secret scanning function (Semgrep Secrets). Semgrep Code examines the source without executing it, and leverages a syntax-aware code search engine to match complex patterns, which can be thought of as semantically grepping code snippets. The platform is designed to identify security vulnerabilities in code such as vulnerabilities, design flaws, and coding errors by using a rule set that can be tailored to an organization’s specific needs or standards. Its ease of use and strong detection capabilities make it a valuable resource for maintaining code quality and security.
By identifying these issues early in the software development process, SAST helps security teams address security concerns before the application is deployed, reducing the risk of security breaches and ensuring a more secure and reliable software product.
Better Together: Harnessing the Power of Semgrep Using Eureka
By integrating Semgrep Code’s SAST capability with the Eureka DevSecOps platform, developers are able to take advantage of the great detection capabilities of Semgrep, centrally manage it along with other security tools, and take advantage of the added visibility into risk by combining the vulnerability data with those from other automated or manual sources such as design review and pentest results to get the full picture.
Interested in Learning More?
Click here to watch the full webinar on how Semgrep seamlessly integrates with Eureka to make your application more secure.

