Security design reviews have no dependency on the application being built or run in an environment. They can also be applied early in the SDLC and provide significant cost savings due to avoidance of costly fixes later on in the application life-cycle.
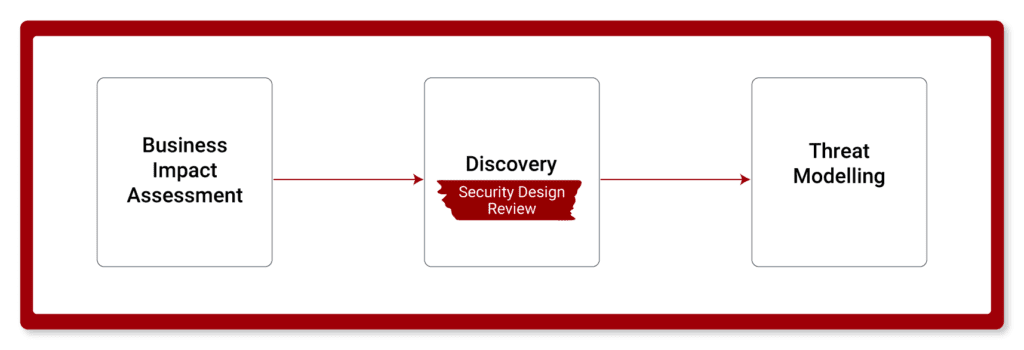
Security Design Review & Threat Modelling
Secure your application from the start
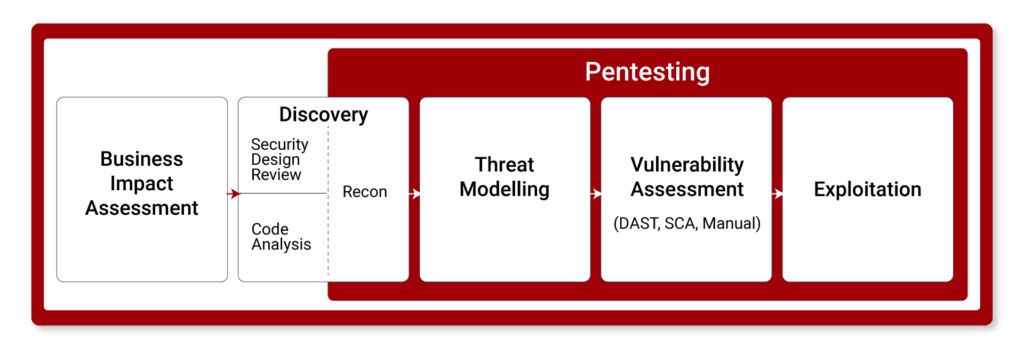
Security Design Review vs Penetration Testing
Pentesting is a limited form of security control. It doesn’t identify the majority of your application’s security issues. For that, you need a Security Design Review and Security Code Review.
In fact, for maximum protection, we recommend our 4-stage Application Security Risk Assessment that includes a Business Impact Assessment, Security Design Review, Security Code Review, Threat Modelling, and Pentesting.
Advantages and Disadvantages of Security Design Reviews
Advantages |
How you can benefit from these advantages |
| Requires no supporting technology | The absence of supporting technology can be an advantage because it enables our staff to rely on their skill and experience to manually review the code to ensure there are no security issues. |
| Early in the SDLC can help avoid costly fixes later on | Identifying and addressing issues early in the Software Development Life Cycle (SDLC) can help avoid costly and time-consuming fixes later on in the pro |
| Encourages a security mindset | Having regular security audits and assessments in place encourages a security mindset among team members, which is an advantage in terms of identifying and mitigating potential security threats and vulnerabilities. |
While Security Design Reviews come with some disadvantages, we can actually address each of them in a unique way
Disadvantages |
How we address these disadvantages |
| Can be time-consuming | To accelerate your time to value, you can leverage our experience and expertise. |
| Supporting material not always available | Our process involves a series of workshops to capture all the required information from your team where previously undocumented material is not available. |
| Encourages a security mindset | Having regular security audits and assessments in place encourages a security mindset among team members, which is an advantage in terms of identifying and mitigating potential security threats and vulnerabilities. |
Where we focus
Look for Potential Threats and Vulnerabilities at the Design Level
Security Design Reviews are a great way to identify threat scenarios that can result in the compromise of your application. Investing in Security Design Reviews early can save you a lot of money, time, and resources.

Business Impact Assessment
Business impact assessments (BIA) are a process by which an organization identifies their digital assets and determines the impact from an attack on the confidentiality, integrity, and availability of those assets.
Most pentesters do not perform business impact assessments.
Instead, a list of issues are provided along with severity ratings that don’t take business context into account. Without knowledge of the digital assets and their impact to the business, these ratings are meaningless.

Discovery Workshop
The discovery workshops aim to review the application or system design, key data allows and functions, identify gaps, and create a blueprint that will prepare us for the next stage – Threat Modelling.
Understanding the architecture of an application is essential to ensuring no potential threats go unnoticed during the
assessment process.
Threat Modelling and Risk Assessment
Using the information from the Discovery Workshop and the Business Impact Assessment, we provide a Threat and Risk Assessment Report. Here we identify key threat scenarios along with impact and likelihood levels assigned to each threat scenario. This allows you to prioritize effectively.
We also provide a list of recommended controls specific to your application and each threat scenario to ensure appropriate security measures are taken into consideration.
Introductory offer
Our team brings global security expertise in the healthcare industry to provide the right-sized solution. To get started, we put together two introductory offers that will help you reduce your business risk, modernize your application securely, and achieve compliance.
Introductory offer
Free one-hour security design consultation
Trying to find out which application security risk is right for you? Our free one-hour security design consultation is a great place to start.
Our team of experienced security analysts have subject matter expertise and knowledge of the latest security threats and vulnerabilities, and apply industry best practices and standards to their views.
Go Above and Beyond with our 4-Stage Comprehensive Application Security Risk Assessment
To go above and beyond, we strongly recommend performing a full assessment, which includes Security Code Review and Security Design Review, Threat Modeling, and Pentesting.