Threat modeling is a proactive approach aimed at identifying potential threat scenarios specific to your application.
Following threat modeling is penetration testing (often referred to as pentesting). This step involves validating each identified threat scenario to determine the actual risks they pose to your business.
In simpler terms, while threat modeling focuses on identifying all possible pathways an attacker could use to breach your system, penetration testing takes the next step by actively attempting to exploit these vulnerabilities.
These two components work together as complementary parts of the broader risk management process.
Consider this analogy – if you were trying to protect valuables in your apartment, logically, the more lines of defense you have, the better protected you are.
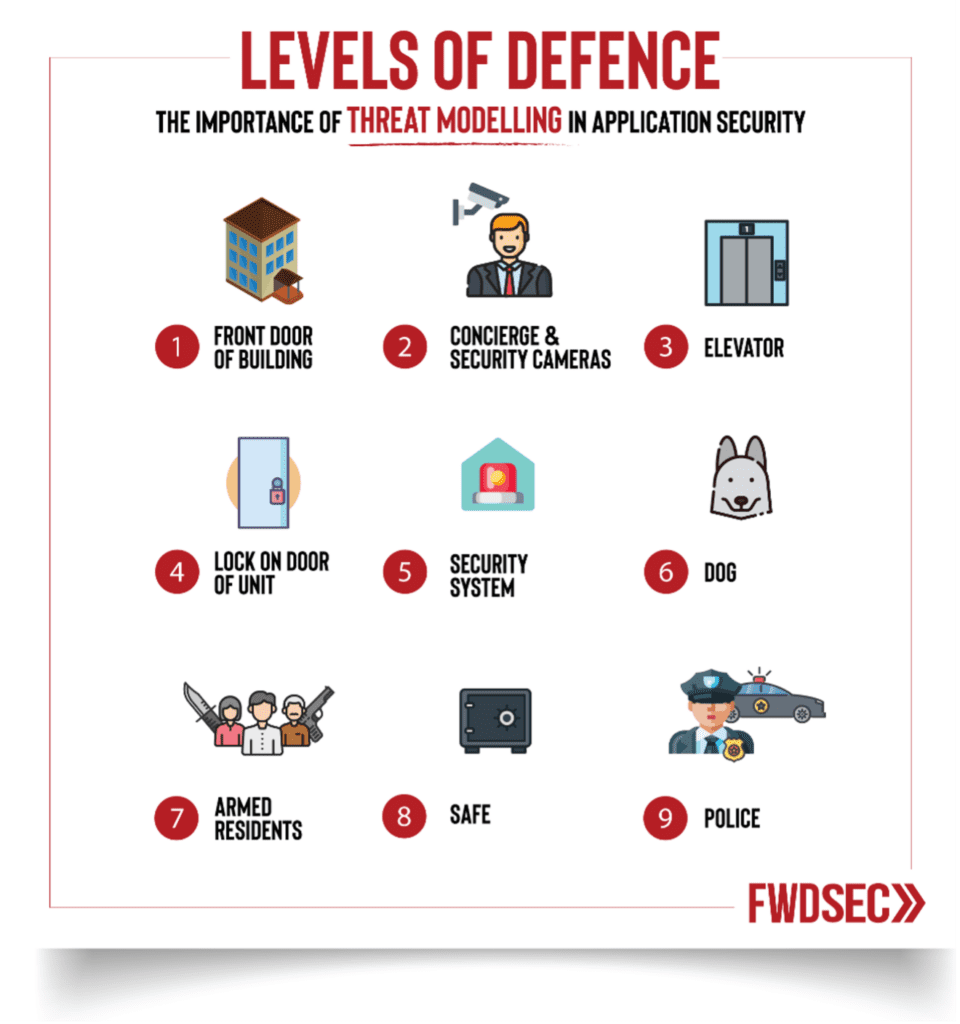
Each security measure can be disarmed or circumvented independently. However, when combined, they create a much stronger line of defence. Similarly, one pathway in isolation may not pose much of a risk, but when combined with another, it can create a significant risk.
Application security mirrors this scenario and threat modelling plays a crucial role in determining your application’s security posture.
Threat modelling aids in:
- Identifying all the security measures individually
- Combining potential attack pathways into comprehensive threat scenarios
- Assessing the likelihood of an attack
- Evaluating the risk posed to the business (taking into account unique business context)
- Establishing priorities for addressing threats
Despite its importance in a comprehensive Application Security Risk Assessment many pentesting providers overlook threat modelling. They often rely on automated scans that come with numerous limitations.
Most pentesters also lack experience as software developers and therefore do not fully understand how software applications are built. As software developers ourselves, we approach code differently. An analogy would be builders and architects inherently have a better understanding of a building’s construction than interior designers or real estate agents. We think like builders and architects because we’ve built code. Therefore, we have a much better understanding of security weaknesses than the average pentester who does not have a background in software development.
Our four-stage Application Security Risk Assessment includes:
- Discovery – We work closely with your team to understand your application’s architecture which is essential for ensuring no potential threats go unnoticed. This may involve hands-on design workshops and comprehensive documentation for your organization.
- Threat Modelling – We go beyond examining individual attack pathways in isolation and create threat scenarios that mimic potential attacks, combining multiple lines of defence to gain a broader understanding of your security posture.
- Pentesting – Using OWASP’s detailed ASVS assurance criteria, our security team builds and executes test cases using both manual and automated methods, including source code analysis where applicable. By adhering to OWASP’s ASVS, penetration testers can systematically assess the security controls and identify vulnerabilities in applications, ensuring a thorough and consistent evaluation. This enables us to verify each threat scenario and identify the actual risks to your business.
- Finalization – Upon completion of our ASRA, your team will receive a detailed report outlining all identified security risks based on impact and likelihood. This report also includes recommended controls to support business risk management decisions.
Penetration testing begins with vulnerability assessment followed by exploitation. The vulnerability assessment involves checking every possible point of entry for vulnerabilities while exploitation attempts to breach these points.
Whether we’re pentesting an IoT device or an application, the process remains the same. We first check for weaknesses then attempt to exploit them. It’s important to note that different standards apply based on what platform we’re testing.
In the finalization stage, we present a comprehensive report detailing all threat scenarios and risks in relation to your specific business context, along with recommendations prioritized according to their importance.
Unlike many pentesting companies who deliver reports listing vulnerabilities without assessing risk based on likelihood and impact, our risk assessment clearly outlines risk allowing your team to prioritize issues effectively.
Our approach is partnership-based. We don’t just hand over the report and walk away as many companies do. They often lack the expertise needed to fix issues because they’re not developers; they’re trained only in identifying problems. At best, they provide generic recommendations.
We are developers who can help you prioritize fixes and offer practical solutions tailored specifically for your application.
If application security is a priority for you, we invite you to connect with us for a free consultation.



