Threat modeling stands as the cornerstone of modern application security, offering a strategic approach that empowers companies to safeguard their digital assets against evolving cyber threats. At its core, threat modeling involves a meticulous examination of an application’s architecture and design to identify vulnerabilities, assess risks, and proactively fortify its defenses against potential exploits.
This systematic process not only bolsters the security posture of applications but also serves as a guiding beacon throughout the development lifecycle, fostering a culture of ‘security by design.’
In this post, we look at the multifaceted significance of threat modeling for application companies, exploring how this practice not only mitigates risks but also ensures compliance, instills trust, and provides a competitive edge in today’s dynamic market landscape.
Threat modeling is crucial for application companies for several reasons. In this post, we discuss 10 benefits to threat modeling.
Identifying vulnerabilities
Threat modeling assists companies in pinpointing potential security vulnerabilities within their applications. By scrutinizing the design and architecture of the application, weaknesses that could potentially be exploited by malicious actors can be proactively discovered.
Risk assessment
Threat modeling enables companies to evaluate the potential risks associated with their applications. This aids in prioritizing security efforts and effectively allocating resources to address the most critical threats.
Security by design
Incorporating threat modeling into the development process fosters the concept of “security by design.” This implies that security considerations are an integral part of the application development lifecycle from inception, rather than being appended as an afterthought.
Reduced security incidents
By identifying and mitigating threats early in the development process, companies can decrease the likelihood of security incidents and data breaches, ultimately saving them from costs and reputational damage associated with such incidents.
Compliance requirements
Many industries and regions have specific regulatory requirements related to data protection and application security. Undertaking threat modeling can help companies demonstrate their commitment to compliance and fulfill legal obligations.
Cost-effective security measures
Threat modeling helps companies prioritize security measures based on threat severity. This ensures resources are invested in areas of utmost importance, making security efforts more cost-effective.
Security awareness
Involving developers, architects, and other team members in the threat modeling process can heighten security awareness throughout the organization. This can foster a culture of security consciousness and a better understanding of best practices for maintaining secure systems.
Third-party trust
Application companies often need to establish trust with customers, partners, and other stakeholders. Demonstrating a robust threat modeling process coupled with a commitment to security can enhance their reputation and make it easier to earn others’ trust.
Competitive advantage
In a competitive market, having a secure application can provide a significant edge over competitors. Customers are increasingly conscious about cybersecurity; hence, maintaining strong security posture can set an application apart from its competitors.
Adaptability and resilience
Threat modeling is not a one-time process; it’s an ongoing activity that evolves as new threats emerge. Application companies that regularly update their threat models are better equipped to adapt to changing security landscapes and maintain resilience against evolving threats.
Threat modeling is vital for application companies to proactively identify and mitigate security risks, comply with regulations, reduce the likelihood of security incidents, build trust, and gain a competitive advantage in the market. It is a fundamental practice for creating and maintaining secure applications.
Automated Threat Modeling with the Eureka DevSecOps Platform
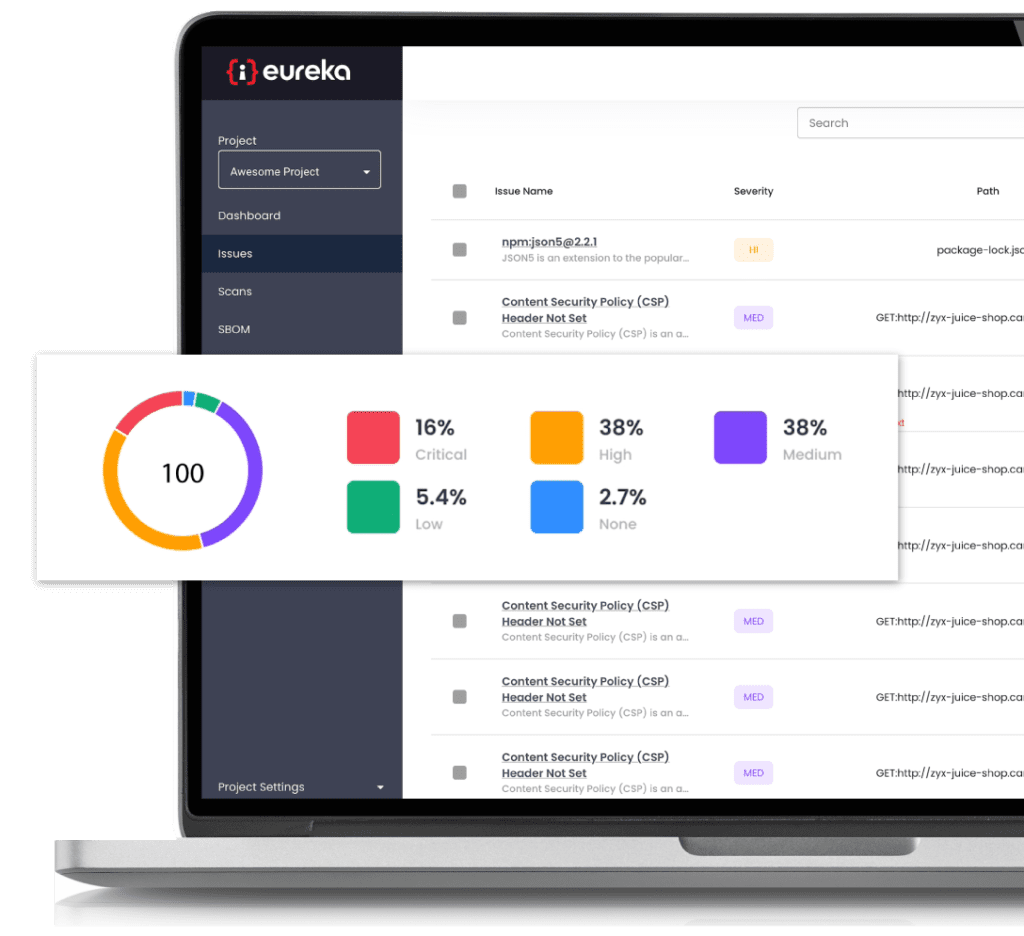
Eureka uses proprietary technology to identify similarities between issues found by different scanners and groups them together. This reduces the number of vulnerabilities that developers need to review, eliminates false-positive fatigue, and allows real issues to be discovered.
To learn more about how our Eureka DevSecOps Platform does automated threat modeling, please contact us to schedule a demo.
Listen and Subscribe to the AppSec Insiders Podcast
The AppSec Insiders is a fun and casual exploration into all things application security. If you haven’t already subscribed, check it out wherever you listen to podcasts.




