| » Ideal for organizations: | Without internal application security expertise, building a traditional, web, or mobile application | Without internal application security expertise, building a traditional, web, or mobile application, and require a higher level of application security maturity through adoption of standards. | Without internal application security expertise, building a traditional, web, or mobile application, and require a higher level of application security maturity through adoption of standards and continuous threat modelling. |
| Technology | | | |
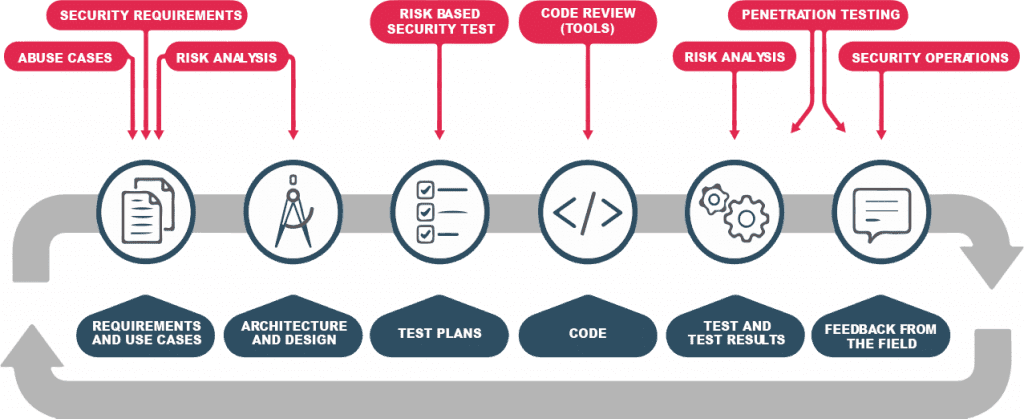
| » Code security analysis: | Find Sec Bugs (Java, Kotlin, Groovy, Scala), Bandit (Python), Brakeman (Ruby on Rails), SonarQube* | Find Sec Bugs (Java, Kotlin, Groovy, Scala), Bandit (Python), Brakeman (Ruby on Rails), SonarQube* | Find Sec Bugs (Java, Kotlin, Groovy, Scala), Bandit (Python), Brakeman (Ruby on Rails), SonarQube* |
| » 3rd party component vulnerability scanning: | OWASP Dependency Check, MergeBase scanner (unlimited scans)* | OWASP Dependency Check, MergeBase (unlimited scans, component level blocking)* | OWASP Dependency Check, MergeBase (unlimited scans, component level blocking)* |
| » Dynamic application security testing: | OWAP ZAP | OWAP ZAP | OWAP ZAP |
| » Infrastructure scanning: | OpenVAS, Nessus | OpenVAS, Nessus | OpenVAS, Nessus |
| » SSL/TLS configuration analysis: | SSLyze | SSLyze | SSLyze |
| People | | | |
| » Dedicated Subject Matter Expert + access to our Center of Excellence: | 12 hrs/month | 18 hrs/month | 24 hrs/month |
| Process | | | |
| » Security Training: | Secure development & threat modelling training (twice per year) | Secure development & threat modelling training (quarterly) | Secure development, threat modelling training and workshops (quarterly) |
| » Adoption of security requirements and processes (based on ASVS) | Basic | Standard | Advanced |