Every time a software development team introduces new code into their Software Development Life Cycle (SDLC), it potentially opens up a security vulnerability. Manual penetration testing can be time-consuming and costly, leading many organizations to deploy automated scanners such as Static Application Security Testing (SAST), Software Composition Analysis (SCA), and Dynamic Application Security Testing (DAST) to identify these vulnerabilities.
Automated security tools are efficient at scanning large volumes of text quickly, identifying security issues, and saving the cost of regular manual penetration testing. However, they have a significant drawback – they generate numerous false positives. A false positive is a harmless or low-risk issue that is reported as suspicious. When these tools report hundreds or thousands of false positives, it can negatively impact the business.
To learn more about these tools, check out our post: How You Can Automate Application Security.
Implications of False Positives
False positives can have several business impacts; here are three major ones:
- False Positive Fatigue: This occurs when developer or security teams are overwhelmed with the tedious task of manually reviewing each issue to determine its severity.
- Security Complacency: False positives can lead dev teams to become complacent about actual threats.
- Lost Revenue: False positives can inadvertently block legitimate traffic that could have resulted in sales or other forms of revenue generation.
Strategies for Reducing False Positives
One effective way to reduce the number of false positives is through proper tool calibration. Even high-quality tools, when improperly configured, can generate many false positives. Therefore, understanding your tool’s settings and adjusting them according to your application’s context is crucial.
Another strategy involves correlating similar findings from different scanners which may help in better identification of actual issues and reducing false-positive fatigue. However, this approach isn’t universally applicable as there could be instances where findings consist entirely of false positives.
Additionally, incorporating threat modeling into your SDLC can help you understand potential attack vectors better and focus your testing efforts accordingly. This can lead to more accurate results and fewer false positives.
Evaluating Solutions for Managing False Positives
While there are many tools available to manage false positives, it’s important to evaluate them based on your specific needs. For instance, the Eureka DevSecOps Platform is an Application Security Orchestration and Correlation (ASOC) platform that allows you to centrally orchestrate all your scanners, correlate the results, and manage your application security threats and risks.
However, other solutions might be more suitable depending on your organization’s size, budget, or specific requirements. Therefore, it’s crucial to explore all possible alternatives, comparing their strengths and weaknesses before making a decision.
Minimizing the Occurrence of False Positives
While automated scanners play a crucial role within an organization’s security strategy, they can generate numerous false positives leading to various challenges. Addressing these issues requires a comprehensive approach involving proper tool calibration, threat modeling, and effective management of scanner outputs. By implementing these strategies effectively, organizations can minimize the impact of false positives on their business operations.
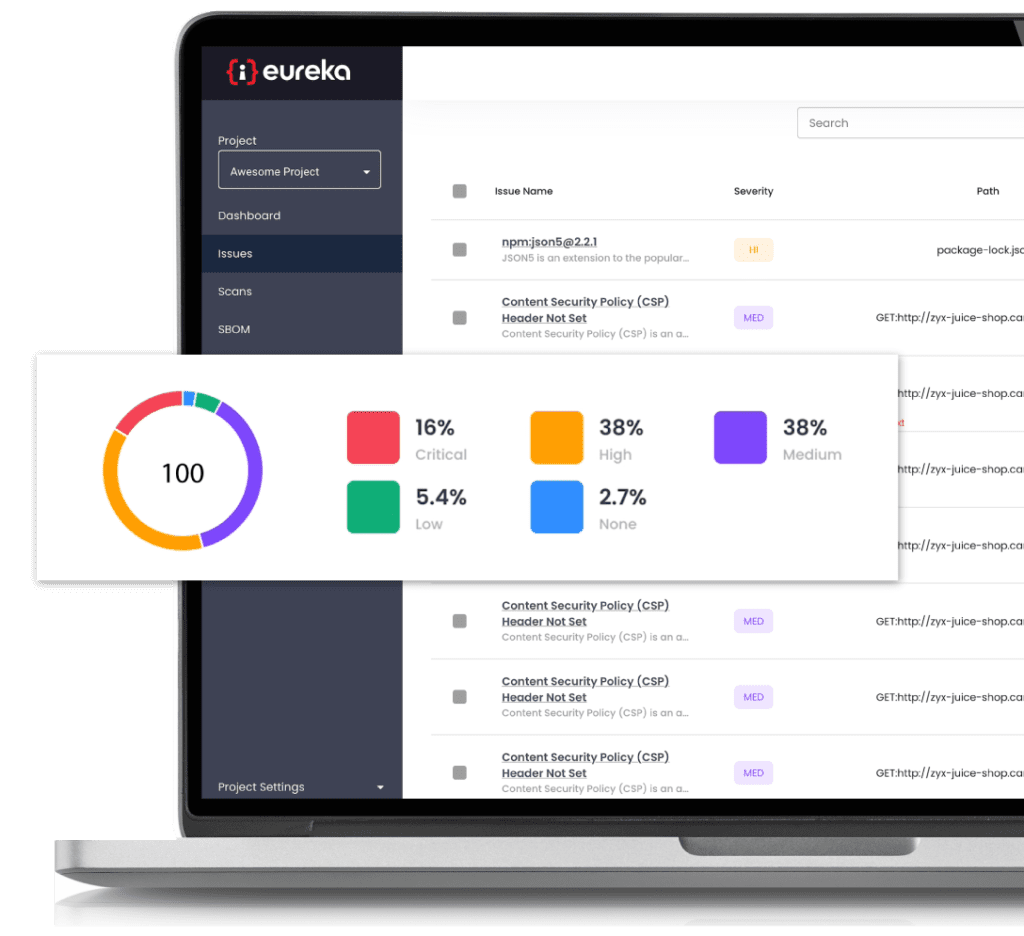
The Eureka DevSecOps Platform makes it easy to integrate and centrally configure multiple scanners (SAST, DAST, SCA). All scanners automatically run inside of the Eureka Agent so you don’t need to deal with individual installation, configuration, and maintenance.
Eureka uses proprietary technology to identify similarities between issues found by different scanners and groups them together. This reduces the number of vulnerabilities that developers need to review, eliminates false-positive fatigue, and allows real issues to be discovered.
To learn more about how our Eureka DevSecOps Platform does automated threat modeling, please contact us to schedule a demo.
Listen and Subscribe to the AppSec Insiders Podcast
The AppSec Insiders is a fun and casual exploration into all things application security. If you haven’t already subscribed, check it out wherever you listen to podcasts.



