Development and security teams rely on automated scanners such as SAST, SCA, DAST, and others to scan applications for bugs and security issues during development and operation. Alongside these automated scanners, teams also conduct manual activities like threat modeling, vulnerability assessments, and penetration testing.
We strongly recommend using more than one high-quality tool that produces fewer false-positives when possible. However, using multiple tools in conjunction with manual testing presents challenges for development teams. These include:
- Lack of standard invocation
- Absence of a global configuration switch
- No central error logging
- Time-consuming installation, maintenance, and patching of several tools
Continue reading: How to get the Most Value from your Security Tools
Standard Invocation
Standard invocations ensure that security procedures are consistently applied across an organization, reducing the risk of human error or deviations from established protocols. They provide a predictable framework for performing security-related tasks which can help identify and resolve security incidents more quickly.
Global Configuration Switch
A global configuration switch improves the efficiency of security operations by providing centralized control over configuring security policies across an organization’s network. It allows administrators to modify security policies quickly in response to new threats or compliance requirements.
Central Error Logging
Multiple tools without a central error log produce reports in different formats that are not normalized. This makes it difficult to triage and remedy issues.
To address these challenges, we created Eureka DevSecOps Platform – a platform that aggregates multiple security scanners into one central error log, normalizes results from both automated and manual sources, provides remediation recommendations.
Installation & Maintenance
Each scanner requires installation into your build agent which can be time-consuming due to the learning curve involved in installing, configuring, maintaining them – this complexity compounds with every additional scanner.
Eureka DevSecOps Platform
Eureka combines all scanners into one central platform, providing a single place for orchestration and management of AppSec tools and threats. It also makes it easier to identify false positives, saving organizations time, money, and stress.
With Eureka, you can:
- Bring Your Own Scanner (BYOS) (commercial or open source)
- Centrally configure and orchestrate your scanners
- Easily integrate your scanners with CI/CD pipelines
- Run the scanning agents inside your own environment
- Keep the scan data in your environment for maximum privacy
- Correlate security issues to reduce false positives
- Filter and push issues to your issue tracking system
- Join security issues to create threat scenarios and assign risk
Read the Case Study: How the Eureka DevSecOps Platform Improved Security for a Data Analytics Company
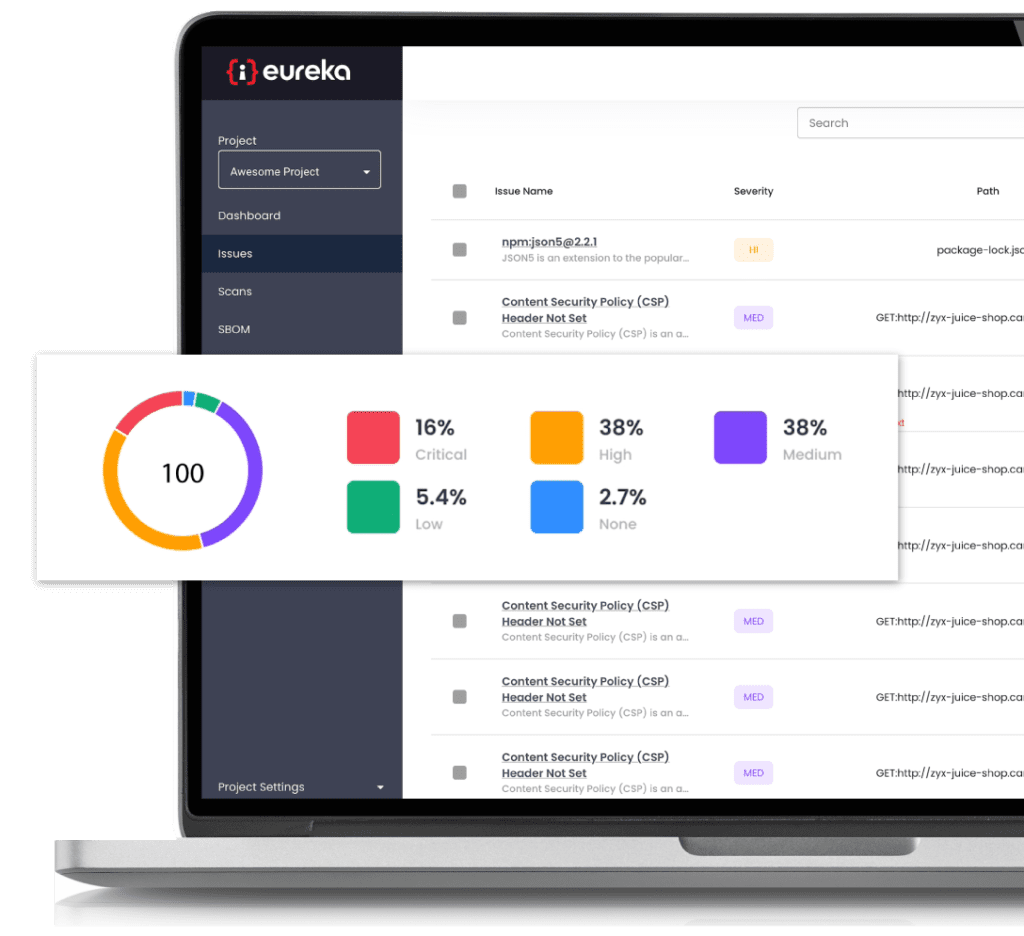
Eureka uses proprietary technology to identify similarities between issues found by different scanners and groups them together. This reduces the number of vulnerabilities that developers need to review, eliminates false-positive fatigue, and allows real issues to be discovered.
To learn more about how our Eureka DevSecOps Platform does automated threat modeling, please contact us to schedule a demo.



